Fullbody Video Cam
With fullbody video call, you upload a reference of the person or peronality or avatar you want to mimic, after that you click on Live.
G
Ginx
Redteam Developer
system.config
01
02
03
04
05
02
03
04
05
1. Executive Impersonation (CEO Fraud / BEC 2.0)
- Scenario: A threat actor, using the deepfake of a CEO or high-level executive, initiates a live video call with a finance employee.
- The Trap: The "CEO" (deepfake) explains an urgent, confidential transaction, possibly showing subtle "stress" or "discretion" through AI-controlled body language. This bypasses email and even voice-only MFA, leading to massive wire transfers or access grants.
2. Targeted Phishing & Espionage
- Scenario: An intelligence agency or corporate spy uses a deepfake of a trusted colleague or a romantic interest to engage a target in a seemingly casual video chat.
- The Trap: The "person" on the call gradually extracts sensitive information, steers the target to malicious links, or persuades them to install "necessary software updates" (malware), leveraging established trust and emotional connections.
3. Ransomware Negotiation & Extortion
- Scenario: After a data breach, a threat actor might use a deepfake of an internal security expert or legal counsel to "negotiate" with the affected company.
- The Trap: The deepfake could display "concern" or "authority" to influence decisions, gain access to recovery systems, or demand ransom payments under extreme duress, making the interaction feel intensely real and urgent.
4. Fraudulent KYC/Identity Verification Bypass
- Scenario: Financial institutions increasingly use video calls for Know Your Customer (KYC) verification.
- The Trap: A sophisticated deepfake could potentially bypass these live checks, allowing criminals to open bank accounts, apply for loans, or access services using stolen identities.
The Benefits to Threat Actors
The advantages of a mature Full-Body Deepfake Video Cam are game-changing for cybercriminals:
- Unprecedented Authenticity: Eliminates the tell-tale signs of static deepfakes or voice-only impersonations (e.g., robotic cadence, lip-sync issues).
- Emotional Manipulation: Allows the threat actor to convey subtle emotions, stress, or urgency through facial expressions and body language, drastically increasing persuasive power.
- Bypasses Multi-Factor Authentication (MFA) Trust: If a live video call is considered the final layer of identity verification, a deepfake shatters that trust. It effectively "shows" the second factor.
- Live Interaction (Adaptive Social Engineering): The deepfake can react in real-time, adapting its responses and emotional display based on the victim's reactions, making the deception far more robust than pre-recorded or text-based attacks.
- Scalability (Future): Once perfected, a single threat actor could operate multiple "deepfake identities" simultaneously, orchestrating complex attacks without needing to be physically present or even speak directly.
The Gallery
Visual breakdown.
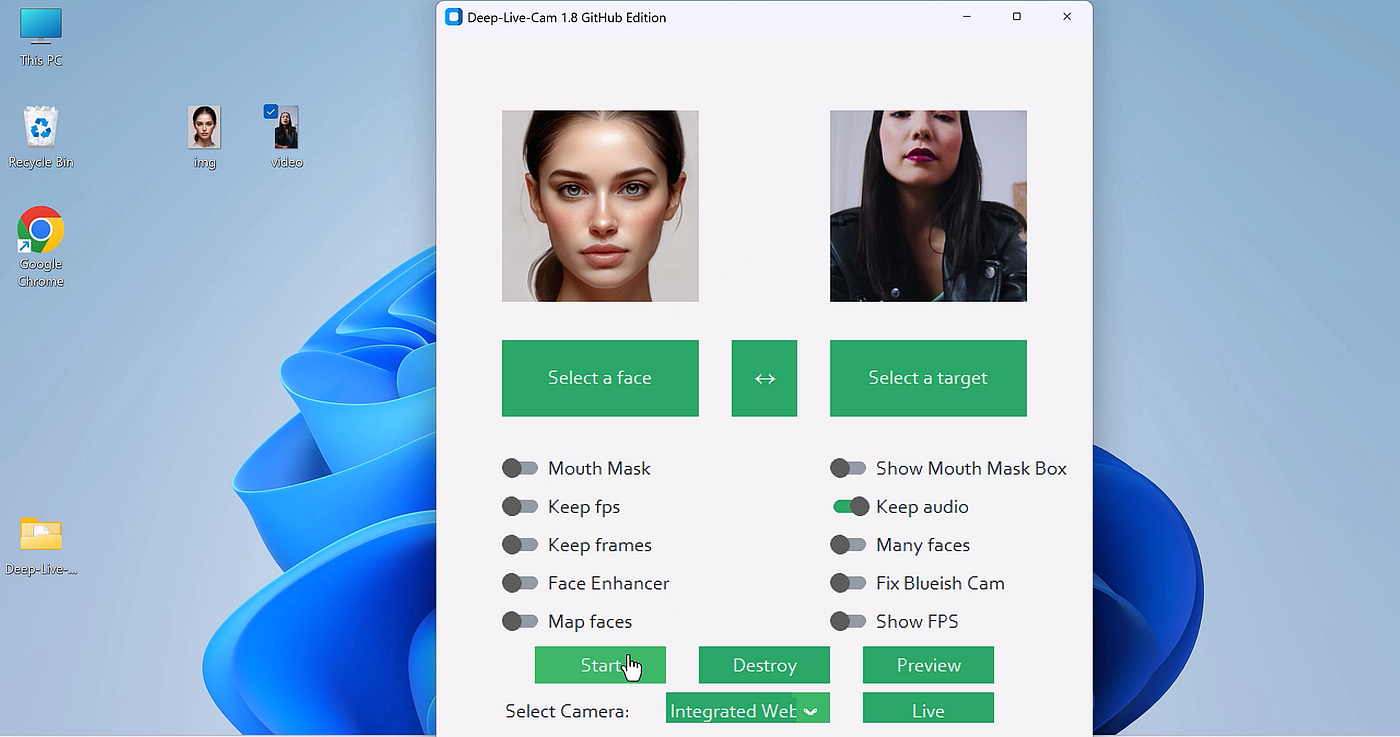
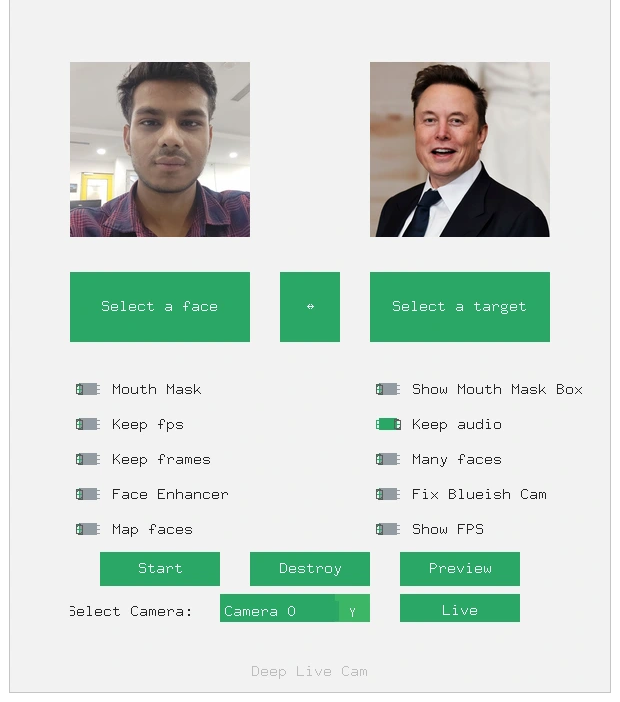
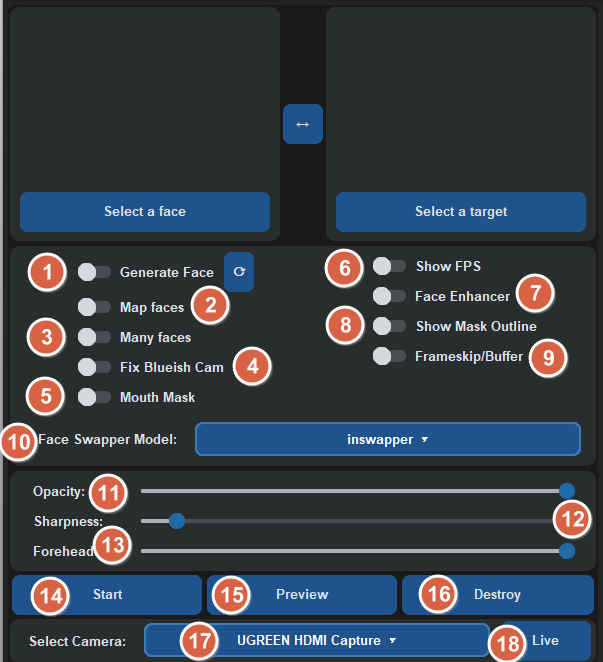
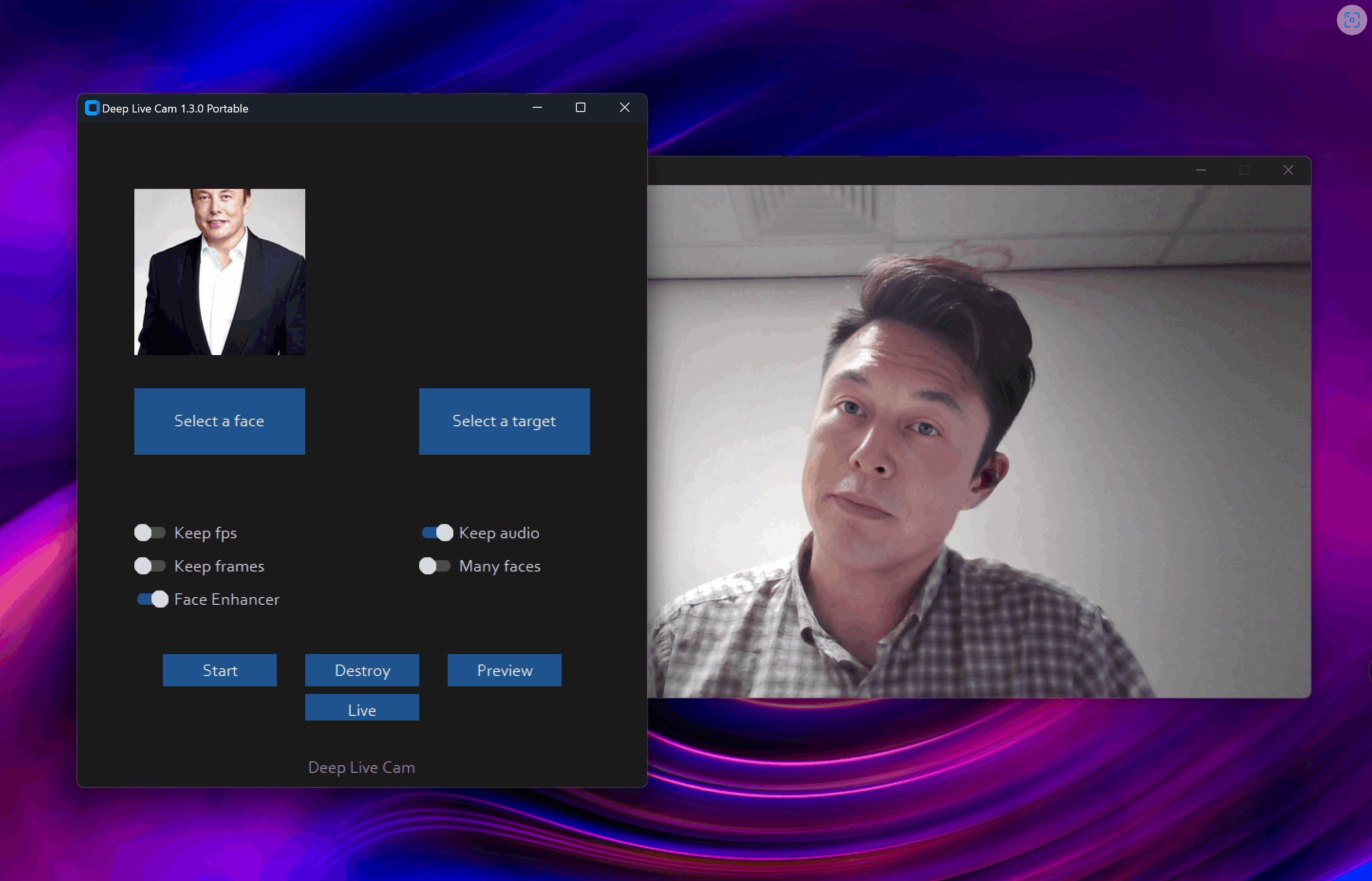
Standard License
£500
one time
24/7 customer care
-
All Gaming Laptops
-
RTX 2050 and above
-
4GB Dedicated
-
Whatsapp
-
Zoom, Telegram
-
etc
